In the realm of wireless communication, two fundamental protocols have been widely used for transmitting data over shared channels: Pure ALOHA and Slotted ALOHA. While both share some similarities, they differ significantly in their approach to handling channel collisions. In this article, we will delve into the key differences between Pure ALOHA and Slotted ALOHA, as well as explore other important protocols used in wireless communication.
Pure ALOHA
In Pure ALOHA, a station (or node) transmits data frames at random intervals, without any prior knowledge of whether the channel is busy or not. This approach leads to high collision rates, as multiple stations may transmit data simultaneously, resulting in errors and retransmissions.
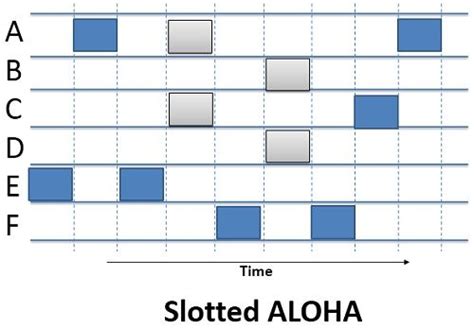
Slotted ALOHA
Slotted ALOHA addresses the limitations of Pure ALOHA by introducing a time-slotted system. Each station transmits data only during specific time slots (or frames), ensuring that collisions are minimized. However, if a collision does occur, it affects the entire frame, making retransmissions necessary.
CSMA (Carrier Sense Multiple Access)
CSMA is another popular protocol used in wireless communication. Unlike ALOHA protocols, CSMA allows stations to sense the channel before transmitting data. If the channel is busy, the station waits until it becomes idle before attempting transmission.
Persistent Method
In persistent method, a station continuously monitors the channel and transmits data as soon as it detects an idle channel. This approach minimizes collisions but can lead to inefficient use of channel resources.
Nonpersistent Method
Nonpersistent method, on the other hand, involves a random wait time before transmitting data when the channel is detected to be idle. While this approach reduces collisions, it may result in longer waiting times and reduced throughput.
p-Persistent Method
The p-persistent method combines elements of persistent and nonpersistent methods. A station continuously monitors the channel and transmits data with a probability p only after detecting an idle channel. This approach balances collision reduction with efficient use of channel resources.
CSMA/CD (Carrier Sense Multiple Access with Collision Detection)
In CSMA/CD, stations detect collisions by monitoring the channel for errors. When a collision occurs, the station waits for a random time before retransmitting data.
Ethernet (802.3) Protocol
The Ethernet protocol, widely used in local area networks (LANs), employs CSMA/CD to manage channel access. The process involves:
- Selecting a persistent method (e.g., 1-persistent or nonpersistent)
- Transmitting data and detecting collisions
- Incrementing the retry count (K) if transmission fails
- Aborting transmission after a maximum number of retries (Kmax)
CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance)
In CSMA/CA, stations delay transmitting data until the channel is detected to be idle for a certain period (IFS). This approach reduces collisions but may lead to longer waiting times and lower throughput.
Wifi (802.11) Protocol
The Wifi protocol uses CSMA/CA to manage channel access. The process involves:
- Detecting whether the channel is busy
- Waiting for an IFS period if the channel is busy
- Detecting whether the channel is busy again
- Waiting for a random time (random backoff) and then transmitting data
- Receiving acknowledgment (ACK) or waiting for a receive timeout (RTO)
- Incrementing the retry count (K) if transmission fails
- Aborting transmission after a maximum number of retries (Kmax)
Controlled Access Protocol
In Controlled Access Protocol, primary and secondary stations communicate with each other through controlled access methods. These methods include:
- Reservation: Sending a reservation frame before transmitting data to ensure channel availability.
- Polling: Primary station sends a SEL signal to request transmission from a secondary station.
Token-passing Network
This network topology uses tokens to control transmission, allowing only token-holding stations to transmit data.
Channelization Protocol
In Channelization Protocol, a single channel is divided into smaller segments (or slots) for efficient use. The three primary types of channelization protocols are:
- FDMA (Frequency Division Multiple Access): Dividing the frequency spectrum into subbands for each station.
- TDMA (Time Division Multiple Access): Allocating specific time slots to each station.
- CDMA (Code Division Multiple Access): Using unique codes to distinguish between stations and enable simultaneous transmission.
FDMA
In FDMA, each station is assigned a specific frequency band for transmitting data. Guard bands are used to minimize interference between stations.
TDMA
In TDMA, each station has a designated time slot for transmitting data, reducing collisions and improving efficiency.
CDMA
In CDMA, all stations can transmit simultaneously using unique codes to distinguish their signals from one another. This approach enables efficient use of channel resources but may require more complex signal processing., wireless communication protocols such as Pure ALOHA, Slotted ALOHA, CSMA, and channelization protocols play a crucial role in managing channel access and minimizing collisions. Understanding the differences between these protocols can help network designers create efficient and reliable wireless networks.